Small businesses should start with surveillance cameras for offices, access control systems for cloud networks, and cybersecurity software like antivirus can help with detecting the issues, controlling, and protecting.
We’ve come so far from the world when protecting business just meant locking the doors and surveillant the files in the office. In the online era, data breaches and threats are the main challenges for startups and large enterprises alike. To combat these challenges, companies need to evolve rapidly and adopt security technologies to protect their assets and people.
We have listed the powerful technologies that can help to evaluate the security levels across all industries in this blog. Let’s get into it!
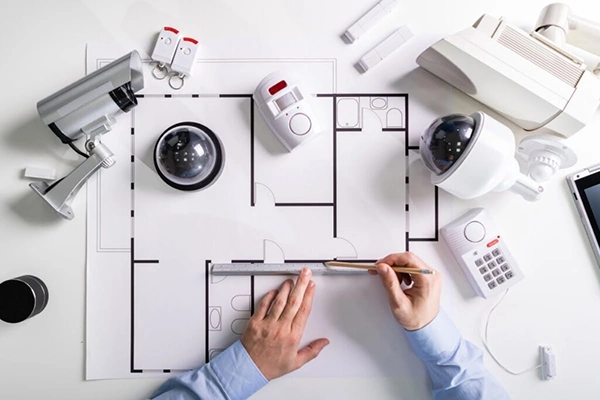
Surveillance cameras are the higher and better versions of CCTV cameras that used to capture grainy images and videos. These cameras record in high definition and cover 360 degrees based on their placement.
You can place these cameras in your office and utilize features like night vision, AI monitoring, facial recognition, and more. The best part is, you can connect with your cloud network and system and access it anytime through your mobile phone or computer.

An access control system is a great form of security. It only allows the assigned individual or the authorized person from the company to access and open the files or data. Through options such as biometrics, key fobs, and mobile access, companies can enhance their management. Plus, it becomes way easier to monitor who’s trying to trespass the security lock.
You receive prompts to allow access and thus, handle the monitoring and surveillance smoothly.
Think of traditional alarms that go on in case of a threat, but more technologically advanced. Modern alarm systems now connect with smart devices and cloud services to provide instant notifications for unauthorized entry, burglaries, or environmental hazards such as smoke and gas leaks.
These alarms can instantly alert both security teams and emergency responders to take action. Moreover, the advanced system now allows protection over remote operations by guarding sensitive data.
You must have noticed the guards checking and scanning at the entrances of schools, offices, malls, and more. Well, it is called weapon detection, and this system has now been modernized for the better.
The newer systems now employ AI, sensors, and imaging technology to identify hidden weapons at access points without manual searches. Weapon detection systems prevent threats and make everyone feel safer.
With the growing number of online threats, it is more crucial than ever to use robust cybersecurity solutions to safeguard business data. You must use antivirus software, endpoint protection, firewall systems, and threat detection technologies to build a multi-layered protection shield. Doing so will make it hard for the intruders to break in.
Plus, the advanced technologies will help to analyze and detect malware, ransomware, and other cybersecurity threats instantly.
The network is the biggest operator of the whole branch of the business. Firewalls, intrusion detection systems (IDS), VPNs, and network segmentation safeguard company information and block unauthorized entry to internal systems.
You can check the weaker points in your security levels and install the network security solution that can strengthen access. As the network is the backbone running the companies, one can not disregard the network security system at all.
Data encryption systems convert the files and assets into encrypted files. Meaning, that these files are converted into non-readable code and can only be decoded with the correct key. From financial documents to business reports, anything can be stored easily using data encryption. This way, you can save the business and have peace of mind that no one can read any data and compromise.
Cloud networks are becoming more popular day and day as more companies are adopting to switch completely online. Switching to the cloud not only makes working easier and effortless but also offers services such as firewall-as-a-service, workload protection, and cloud access security brokers (CASBs). These tools help keep digital assets on platforms like AWS, Azure, or Google Cloud secure and compliant.
Mobile security management tools are specially designed to protect mobile smartphones and all the apps integrated into them. These solutions, like mSPY, can be installed on Android or iOS to provide control over screen time, apps, access detection, security locks, and more.
Mobile security solutions help businesses to enforce a layer of security and guard against data loss from lost or compromised devices.
The purpose of identity and access management is to give access only to the right people at the right time. It uses various techniques like multifactor authentication, single sign-on, role-based access control, and keyword login to strengthen the security system. It offers advanced features that can be used by the IT team of the company to manage identities and prevent credential theft.
Auditing the access management system and reviewing the authorized profiles regularly ensures that only verified users gain access.
No matter how strong the security level is, you must always have a crisis management and incident response plan to activate in case of data theft and breach. These can include backup access, communication flows, and strong steps to restore the data.
Regular checking can assist your team in reacting quickly and composedly during actual emergencies. An effective IRP reduces harm, accelerates recovery, and guarantees adherence to regulations.
Having the best-in-class technology can not save your business singlehandedly. Your employees must have digital literacy, knowing how to leverage and use the software and systems wisely.
Every company should conduct employee training sessions to instruct them not to open phishing emails or use weaker passwords. Empowering the workforce with the latest tools and providing the right knowledge can improve engagement in the company and make people a proactive part of the security strategy.
You should also take the necessary steps to upgrade your physical security measures. Anyone can break into the office and intercept the data and assets; however, the right tools help to avoid such circumstances. You need to install surveillance infrastructure, smart locks, security personnel, reinforced entry points, and motion-detecting lights in the building to track everything.
The remote lock system is more effective, and it sends alerts to inform about the after-hour movements.
Companies need to organize security training programs at all levels. Let’s say, developers must know how to protect their code, app developers know how to shape the future, HR must learn to shield sensitive employee information, and more. Every department or hierarchy must get a targeted training program that they can utilize to elevate security levels and company compliance.
Quick reporting of any mishap helps to reverse the effects almost instantly without causing too much harm. You must leverage incident reporting tools that alert and diagnose fraud early. These software programs are cloud-based and can be accessed over a smartphone, enabling people to send alerts and address issues in real-time.
These tools contain multiple useful features such as reporting incidents, uploading images, or tagging departments so that the matter can be resolved on priority.
Risk assessment tools audit the security layers of the business operations, find loopholes, and generate the best possible solution to fix the issues. These software programs are built with artificial intelligence and machine learning to evaluate the vulnerabilities and understand the situation.
The job of a risk assessment solution is to perform continuous scans to identify obsolete software, incorrectly set configurations, and unusual behavior.
Installing multiple security systems, reviewing them, and updating them one after the other can be a tiring task. This is where an integrated security system comes in. It is a single-centralized platform that can handle all the security layers in one place.
You can now link and manage your CCTV cameras, data encryption tools, network security solutions, and risk management software in one place. All you will see is a single dashboard and the ability to monitor each security option efficiently.
Threat intelligence platforms work tirelessly to collect information about new cyber threats. It analyses the merging threats and decodes the methods to safeguard against them. The platforms use closed and open-source intelligence to protect businesses from attacks before they happen.
Remaining one step ahead of cybercriminals demands continuous vigilance, and threat intelligence servers are the best partners.
Small businesses should start with surveillance cameras for offices, access control systems for cloud networks, and cybersecurity software like antivirus can help with detecting the issues, controlling, and protecting.
It is important to audit the security system annually or biannually. This move allows spotting the vulnerabilities, updating to the advanced version and providing better solutions.
You can get one central platform and link all the installed security methods. The integrated security solutions offer a dashboard from where companies can monitor and review the issues and fixes.
