It takes 20 years to build a reputation and a few minutes of cyber-incident to ruin it. – Stephane Nappo
Are you going to implement VoIP in your business? According to Wikipedia, “Voice over Internet Protocol (VoIP), also known as IP telephony, refers to a set of technologies used for voice communication sessions over Internet Protocol (IP) networks, such as the Internet.”
It’s used everywhere, and companies/businesses are no exception. But you might not be aware of the security risks surrounding it. VoIP is quite easy to target which can cause damage to your company, what can be done?
I’ll tell you why you should be a top priority if you are implementing VoIP, and things you can do to make it robust.
Cyberattacks are more common than you might anticipate. They are one of the major causes that affect organizations financially. Hackers can easily get a hold of your VoIP with several methods.
Like phishing, eavesdropping, and DDoS (distributed denial-of-service) attacks. But what will happen if they can succeed with any of the techniques? They can leak sensitive information for the whole world to see or cause major losses to commercial enterprises.
Companies need to invest in strong security measures, like encryption protocols, security audits, multifactor authentication, and more. This would minimize the risk of cyberattacks and over time, it will get stronger.
Additionally, we recommend researching Top-rated VoIP systems that have security features such as end-to-end encryption or real-time monitoring. Choosing a reliable VoIP provider can make a significant difference and protect your communication infrastructure.
You might not believe it, but VoIP-related frauds have also increased. What attackers do is make unauthorized calls, taking full benefit of any possible vulnerabilities and causing financial losses.
For example, there is a toll fraud, where attackers use your VoIP account and make long international calls. Companies have received soaring phone bills, and they didn’t know that something like this was happening.
In the infographic below, you can see the key categories that are targeted by fraud attackers.
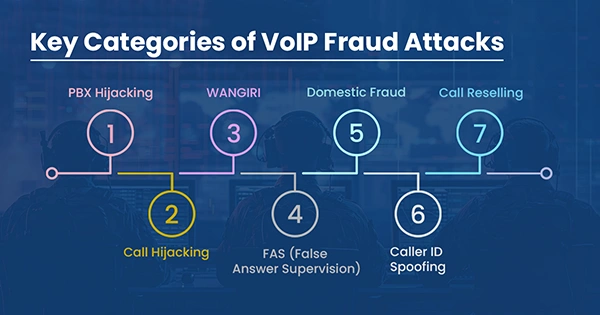
To prevent this, you would need strong security measures. While strong passwords, firewalls, and firmware updates will be helpful, I will also recommend you integrate RBAC controls, to manage the accessibility of call logs and VoIP settings.
If your business experiences service interruptions, customers will start questioning you, and your corporate operations will be affected. Cyber Attackers can make VoIP systems inaccessible, which can lead to downtime and financial losses.
If you want to keep your firm’s operations and reliability at a standard level, you should have good security strategies like backup servers and failover systems. I’ve mentioned earlier, I’ll say it again, choosing a reliable VoIP provider is a must.
If your provider has strong security protocols and infrastructure, the communication will not be interrupted in case of a cyberattack.

Complying with data security law is also necessary. But why? There are several reasons for this, including:
VoIP communications usually contain sensitive customer and business data that must be protected strongly to be compliant with regulations like GDPR and HIPAA. Individuals need to do everything in their power to ensure that nothing goes out of their organization, or they’ll be in big trouble. —- This does not include only securing the data itself but also making sure users have clear, informed permission before it’s collected or used, as outlined in the requirements for GDPR consent.
Use encryption, access controls, and secure data storage solutions. This is the only way to stay compliant with law and industry regulations.
VoIP systems contain sensitive data, which can be confidential conversations between clients, employees, business partners, or consumers.
If entities haven’t taken proper precautions or security measures, they can easily lose all the data to cybercriminals as they’ll be able to intercept calls, manipulate call data, or leak voicemail messages.
This is a serious breach of privacy, but this can be tackled if you use encryption technologies such as SRTP and TLS. This way, you’ll be able to protect your customers and employees’ privacy.
These are the protocols that encrypt voice data and make intercepting/manipulating conversations very hard for hackers.
DID YOU KNOW?
In 2023 the global VoIP market was valued at $112.9 billion in 2023!

There are external threats, but there are also insider threats and it is quite serious. Your employees can mishandle sensitive data or be the victim of phishing attacks.
Businesses should organize regular security training, have strict access controls, and use logging mechanisms to monitor user activities. Company owners need to educate their employees on this topic so they can recognize an online threat and how it can be dealt with.
This is the only way to improve the whole security of VoIP communications. VoIP can benefit your venture in several ways and is quite useful, but it comes with certain risks that can’t be ignored or there will be severe consequences.
Each business should take precautions and protect both its customers and employees, as strong data privacy is a key to success in the market.
